You are not logged in.
- Topics: Active | Unanswered
#1 2021-07-11 15:56
- Tolkem
- Member
- Registered: 2019-10-06
- Posts: 487
How to recover/restore forgotten/lost password
Hi everyone! Hope you're all having a nice life! ![]()
Today, I'll share with you a method to restore/recover your lost/forgotten password, that is, the password you use to log in as well as execute sudo commands in the terminal.
1. Turn on your pc, and when Q4OS starts booting press the shift key, so you can access the grub console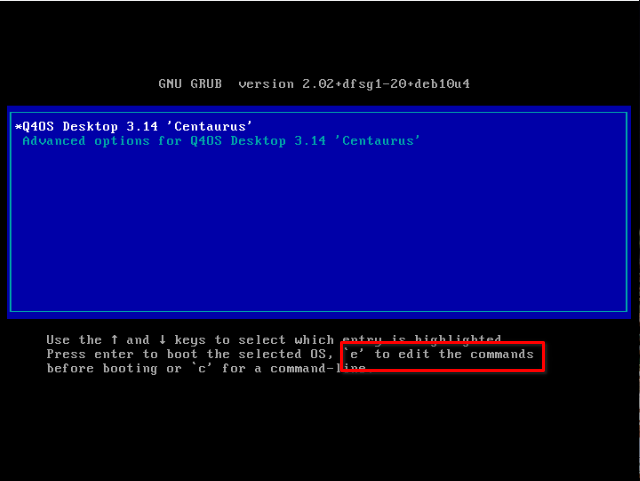
2. You may have noticed the highlighted line in the img above, well do as it says and press e to edit boot options, you should see this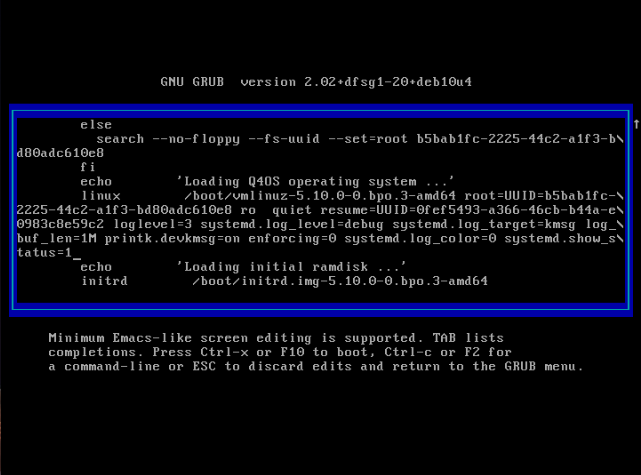
3. Scroll down using the arrows keys, and right after where it reads status=1 add the following
rw init=/bin/bash so it looks like this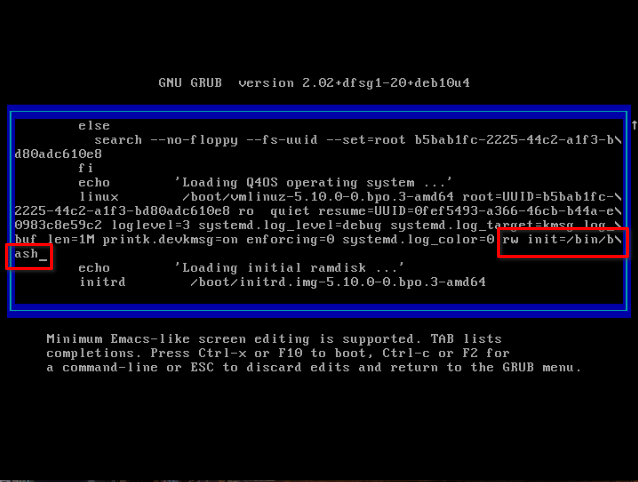
4. Hit Ctrl + x to save the changes and boot to a command line console
5. Now, type passwd followed by your username, and press Enter, for example, I did passwd tolkem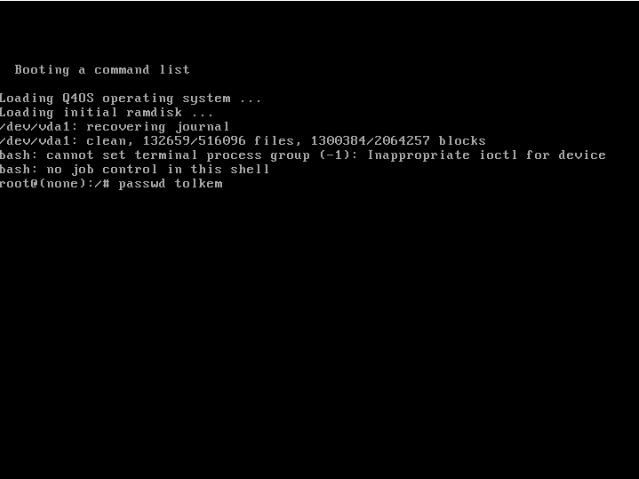
6. You'll be prompted to type in, and confirm your new password, do so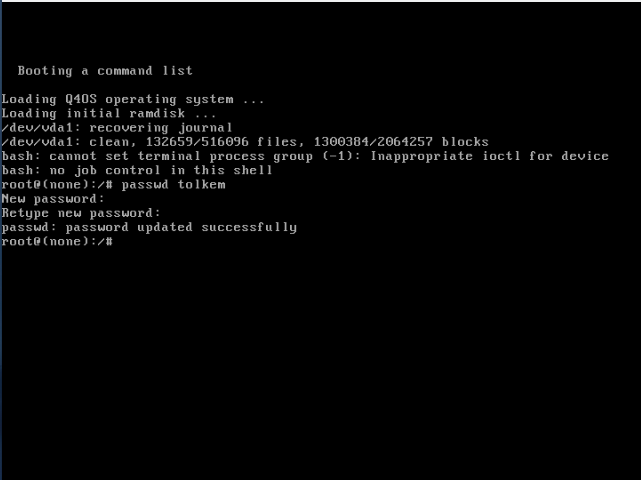
7. Once the password has been updated/restored successfully, type in sync and press Enter, then type in reboot -f and press Enter again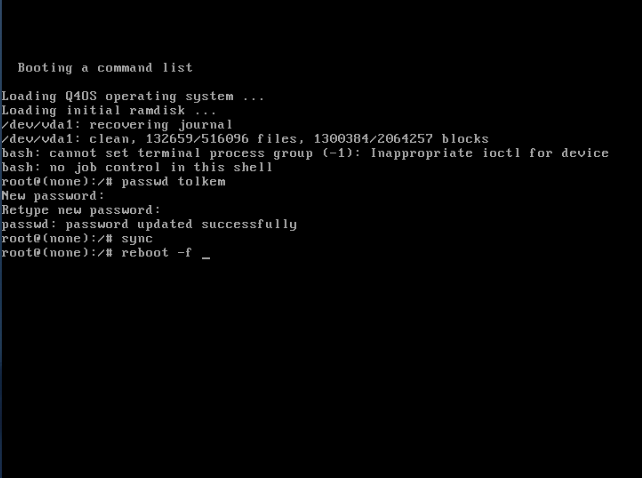
At this point, Q4OS should start normally, and you should be able to log in with your new password in TDM, like I did


Well, that's it. Pretty easy, isn't it? Now you know how to recover/restore your lost/forgotten password without having to boot a Live USB, mount partitions, chroot and all that. ![]()
NOTE: You may or may not have noticed that while I said in step 3 "Scroll down using the arrows keys, and right after where it reads status=1 add the following rw init=/bin/bash" however, in the next img in step 4 you can see that line is actually right after log_color=0, well, thing is, that key for "=" doesn't work in my keyboard if using an English layout, like in grub, it does in my language(Spanish) but I've no idea how to change that for grub. So I had to delete the status=1 line to reuse the "=" symbol, but I think it should work by just adding the line right after that. I just wanted to mention that, so you don't get confused. ![]()
Last edited by Tolkem (2021-07-11 16:06)
Offline
#2 2021-07-12 10:14
- q4osteam
- Q4OS Team

- Registered: 2015-12-06
- Posts: 5,029
- Website
Re: How to recover/restore forgotten/lost password
Thanks for the well arranged instructions. We have created new Q4OS documentation project on Github https://github.com/q4os/q4os-documentation , so you are more then welcome to contribute there and create a new documentation in html format, so we may include it into the official Q4OS documentation.
Offline
#3 2021-07-12 14:15
- Tolkem
- Member
- Registered: 2019-10-06
- Posts: 487
Re: How to recover/restore forgotten/lost password
Glad to help. Thanks for the invitation, I will participate and contribute.
Offline
#4 2021-07-13 09:28
- Dai_trying
- Member

- From: UK
- Registered: 2015-12-14
- Posts: 2,994
Re: How to recover/restore forgotten/lost password
I just wanted to note that this highlights the single most important reason to use encryption on your personal files, otherwise any person who gains physical access to your machine can change the password and gain full access to everything you have...
Offline
#5 2021-07-13 12:50
- q4osteam
- Q4OS Team

- Registered: 2015-12-06
- Posts: 5,029
- Website
Re: How to recover/restore forgotten/lost password
... person who gains physical access to your machine can change the password and gain full access to everything you have...
Yes, this generally applies to any operating system that does not have encrypted data.
Offline
#6 2021-07-13 13:00
- Dai_trying
- Member

- From: UK
- Registered: 2015-12-14
- Posts: 2,994
Re: How to recover/restore forgotten/lost password
Yes, absolutely, I only posted to remind any users of the physical security risks of their machines ![]()
Offline
#7 2021-07-13 14:18
- Tolkem
- Member
- Registered: 2019-10-06
- Posts: 487
Re: How to recover/restore forgotten/lost password
I just wanted to note that this highlights the single most important reason to use encryption on your personal files, otherwise any person who gains physical access to your machine can change the password and gain full access to everything you have...
Good point. However, I think it's important too to let users know that most home users don't need an encrypted device, unless they are some military consultant/advisor, politician(remember Hillary?), bank manager, in other words, if you're a user with no access to sensible data that can compromise you or the people/organization/government you work for, then you probably don't need encryption. An encrypted device can be a PITA if for whatever reason you can't access your device, as it makes it more difficult to recover your data, and if somehow you forgot/lost your master key, then you won't be able to do it, thus being forced to reinstall the OS, and losing your data. This is a good article on the subject https://hexnode.medium.com/what-is-devi … 019640b825
An excerpt:
When should you use Hard-Drive Encryption?
Before implementing a Hard-Drive Encryption policy, it may be a good idea to take heed of this advice — would you rather lose your data than have it all exposed? — If the answer is no, then you should probably think twice before setting up HDE for your enterprise devices.
Organizations that store private or confidential information on their devices can benefit a lot from encrypting their hard drives. Companies that need to maintain — GDPR, HIPAA, CJIS compliance — will have to make use of HDE policies for their devices.
Note that it refers to corporate environments, where "any person" may have the knowledge and skill to gain access to your corporate/sensible data.
Last edited by Tolkem (2021-07-13 14:19)
Offline
#8 2021-07-13 14:33
- Midas
- Member

- Registered: 2017-12-15
- Posts: 234
Re: How to recover/restore forgotten/lost password
Tolkem makes a very good point about encryption, IMHO. ![]()
Offline
#9 2021-07-14 09:06
- Dai_trying
- Member

- From: UK
- Registered: 2015-12-14
- Posts: 2,994
Re: How to recover/restore forgotten/lost password
Good point. However, I think it's important too to let users know that most home users don't need an encrypted device, unless they are some military consultant/advisor, politician(remember Hillary?), bank manager, in other words, if you're a user with no access to sensible data that can compromise you or the people/organization/government you work for, then you probably don't need encryption. An encrypted device can be a PITA if for whatever reason you can't access your device, as it makes it more difficult to recover your data, and if somehow you forgot/lost your master key, then you won't be able to do it, thus being forced to reinstall the OS, and losing your data.
As far as being a "PITA" when recovering a system, that is the point of encrypting your files containing sensitive date isn't it? Ease of use means ease of access to anybody having access to your device(s). I'm not a fan of complete HDD (SSD) encryption, but as you have shown how easy it is for anybody with access to your machine to gain full access to the data it contains, it would surely make sense to advise of a simple security measure to keep your sensitive data safe (if you have any).
But my point has been made in my first response, I'm happy that any user can read it and make their own mind up, after all I don't care if any individual user decides not to encrypt their data but I do believe they should be reminded of the consequence in order to make an informed decision.
Offline
#10 2021-07-14 14:27
- Tolkem
- Member
- Registered: 2019-10-06
- Posts: 487
Re: How to recover/restore forgotten/lost password
As far as being a "PITA" when recovering a system, that is the point of encrypting your files containing sensitive date isn't it? Ease of use means ease of access to anybody having access to your device(s). I'm not a fan of complete HDD (SSD) encryption, but as you have shown how easy it is for anybody with access to your machine to gain full access to the data it contains, it would surely make sense to advise of a simple security measure to keep your sensitive data safe (if you have any).
But my point has been made in my first response, I'm happy that any user can read it and make their own mind up, after all I don't care if any individual user decides not to encrypt their data but I do believe they should be reminded of the consequence in order to make an informed decision.
It should be a PITA for someone else, not for you. I agree, people should make their decisions based on their best interests, and that's exactly my point, does someone who uses his/her pc just to listen to music, watch some videos and movies, play some games, in other words, does a regular human being with no access to sensible data that can compromise his/her or someone else's integrity need encryption? I don't think they do, I don't need it, and I don't use it.
Regarding that "how easy it is for anybody with access to your machine to gain full access to the data it contains", seriously? Anybody? I don't know a single person in my social/work circle who knows how to crack a device, let alone how to do the procedure explained in this tutorial, not my friends, not my family, not my co-workers, maybe yours is a bit different, but I bet most regular human beings are in a similar situation like I do; they're the only ones who know what a grub screen is. So "anybody" might not be quite accurate, maybe you mean "anybody with the knowledge and skill", and I'm pretty sure people who are in such a situation, and they know anybody in their social/work environment might have the knowledge and skill to gain access to their data, are using encryption.
Offline
#11 2021-07-14 14:46
- Dai_trying
- Member

- From: UK
- Registered: 2015-12-14
- Posts: 2,994
Re: How to recover/restore forgotten/lost password
It should be a PITA for someone else, not for you.
You should be able to remember your own password ![]()
I agree, people should make their decisions based on their best interests, and that's exactly my point, does someone who uses his/her pc just to listen to music, watch some videos and movies, play some games, in other words, does a regular human being with no access to sensible data that can compromise his/her or someone else's integrity need encryption? I don't think they do, I don't need it, and I don't use it.
I'm not saying you have to, simply pointing out that if it is that easy to change a user password and gain full access to the system that it would be good practise to use some form of encryption to keep anything you need kept private.
Regarding that "how easy it is for anybody with access to your machine to gain full access to the data it contains", seriously? Anybody? I don't know a single person in my social/work circle who knows how to crack a device, let alone how to do the procedure explained in this tutorial, not my friends, not my family, not my co-workers, maybe yours is a bit different, but I bet most regular human beings are in a similar situation like I do; they're the only ones who know what a grub screen is. So "anybody" might not be quite accurate, maybe you mean "anybody with the knowledge and skill", and I'm pretty sure people who are in such a situation, and they know anybody in their social/work environment might have the knowledge and skill to gain access to their data, are using encryption.
Linux itself is not wide enough spread to be common knowledge to "anyone" but I would not like to take that risk with my personal data, emails, any website passwords that are saved in your web-browser etc, etc, etc... Of course anybody is free to use their own judgement and ignore my offered advice, after all it is their data mot mine, their machine not mine, their identity not mine...
And please remember I am not saying your advice is bad! it is the simplest way to reset your user password and is easily followed and implemented, I'm simply saying users might want to think about the security of their data.
Offline
#12 2021-07-14 15:08
- aluma
- Member
- From: Ukraine
- Registered: 2018-03-12
- Posts: 136
Re: How to recover/restore forgotten/lost password
For a real Linux user (who only has Linux installed), it costs nothing to close this loophole.
It is enough to set "GRUB_TIMEOUT = 0" in /etc/default/grub and reinstall grub.
PS.On my computer, it is done, other options for many years have been practically unnecessary and the delay in nothing.
Last edited by aluma (2021-07-14 15:25)
Offline
#13 2021-07-14 15:48
- Tolkem
- Member
- Registered: 2019-10-06
- Posts: 487
Re: How to recover/restore forgotten/lost password
Tolkem wrote:It should be a PITA for someone else, not for you.
You should be able to remember your own password
I'm not saying you have to, simply pointing out that if it is that easy to change a user password and gain full access to the system that it would be good practise to use some form of encryption to keep anything you need kept private.
I agree. People who decide to encrypt their devices should save their master key someplace safe, like in a piece of paper, if they somehow lost it or forgot it, then it'd be a PITA to access their own devices.
Linux itself is not wide enough spread to be common knowledge to "anyone" but I would not like to take that risk with my personal data, emails, any website passwords that are saved in your web-browser etc, etc, etc... Of course anybody is free to use their own judgement and ignore my offered advice, after all it is their data mot mine, their machine not mine, their identity not mine...
And please remember I am not saying your advice is bad! it is the simplest way to reset your user password and is easily followed and implemented, I'm simply saying users might want to think about the security of their data.
I know that's not what you're saying. ![]() And I agree, people should make their own decisions, I just think saying "anyone" needs encryption might lead users to think they do, and maybe they don't, it's up to them. I guess what I'm trying to say is: it is a good idea to use encryption, just be aware of what implies such procedure, and take the necessary precautions accordingly: keep your master key someplace safe, because if you lose it, you might have problems to recover your data.
And I agree, people should make their own decisions, I just think saying "anyone" needs encryption might lead users to think they do, and maybe they don't, it's up to them. I guess what I'm trying to say is: it is a good idea to use encryption, just be aware of what implies such procedure, and take the necessary precautions accordingly: keep your master key someplace safe, because if you lose it, you might have problems to recover your data.
For a real Linux user (who only has Linux installed), it costs nothing to close this loophole.
It is enough to set "GRUB_TIMEOUT = 0" in /etc/default/grub and reinstall grub.PS.On my computer, it is done, other options for many years have been practically unnecessary and the delay in nothing.
If you press the Shift key while booting "GRUB_TIMEOUT = 0" in /etc/default/grub" won't matter, you'll get to grub menu anyway. By the way, you don't need to reinstall grub, just update its configuration file.
sudo update-grubOffline
#14 2021-07-14 16:17
- aluma
- Member
- From: Ukraine
- Registered: 2018-03-12
- Posts: 136
Re: How to recover/restore forgotten/lost password
"If you press the Shift key while booting "GRUB_TIMEOUT = 0" in /etc/default/grub" won't matter, you'll get to grub menu anyway. ..."
Lenovo s205, does not respond to key presses, immediately starts loading the OS
Offline
#15 2021-07-14 16:52
- Tolkem
- Member
- Registered: 2019-10-06
- Posts: 487
Re: How to recover/restore forgotten/lost password
"If you press the Shift key while booting "GRUB_TIMEOUT = 0" in /etc/default/grub" won't matter, you'll get to grub menu anyway. ..."
Lenovo s205, does not respond to key presses, immediately starts loading the OS
It has to be done quickly.
Offline